
Julian Assange Skyped into the TMC conference to discuss “The Use and Abuse of Whistleblowers” with Juan Gonzales, Democracy Now!; Gavin MacFadyen, Centre for Investigative Journalism; and Bea Edwards, Government Accountability Project.
They use burner phones as they cross borders. They buy old Lenovo computers because there are fewer backdoors into those computers that allow surveillance.
They are not spies or criminals. They are investigative reporters trying to get on-the-ground stories to help us understand and sometimes change our world.
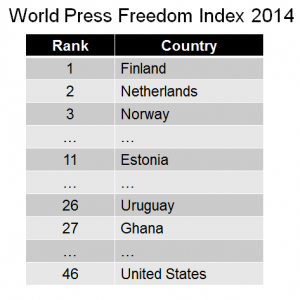
Last week, The Media Consortium and IIT Chicago-Kent College of Law joined forces to describe the challenges that reporters face in an era when intelligence agencies such as the National Security Agency and corporations such as Google spy on what each of us is doing on our digital devices. At the joint workshop, Josh Stearns of Free Press and the Freedom of the Press Foundation reported on how many journalists had been killed and jailed in last year. And it’s not just a problem abroad. According to the World Press Freedom Index, the United States has slipped to number 46 in a ranking of countries on how much freedom it gives its reporters, well below even countries such as Ghana and Uruguay. amalia deloney of the Center for Media Justice described how surveillance in general disproportionately affects people of color. She showed a slide of a police tower that one might have guessed was situated in Guatemala or another oppressive nation. Instead, it was in a primarily African-American neighborhood in Charlotte, North Carolina.
What information is the NSA collecting about activists, reporters and you? The NSA gathers the phone numbers, locations, and length of virtually all phone calls in the United States. It collects records of nearly everything you do online, including your browsing history and the contents of your emails and instant messages. It can create detailed graphs of your network of personal connections. It can create phony wireless connections in order to access your computer directly. It can intercept the delivery of an electronic device and add an “implant” allowing the agency to access it remotely.
Companies, too, undertake surveillance. Investigative reporter Adam Federman found that the “American Petroleum Institute (API) paid private global intelligence firm Stratfor more than $13,000 a month for weekly bulletins profiling activist organizations and their campaigns … from energy and climate change to tax policy and human rights, according to … WikiLeaks in 2012.” Federman reported that when a community group of 10 people met to screen environmental films and attend local environmental forums, a private security firm identified them as likely planning an eco-terrorism attack. A bulletin with the group’s information – where and when they met, and upcoming protests – was sent to the Pennsylvania Department of Homeland Security alongside information about other groups such as Al-Qaeda affiliated groups and pro-life activists.
 When reporters cross borders, they are at increased risk of surveillance. As the 2013 federal district court case of Abidor v. Napolitano showed, border agents in much of the U.S. can search, copy, and detain a U.S. citizen’s laptop computer, cell phone, or other electronic device even when the agents have no reason to suspect any wrongdoing. The court held that the government had reasonable suspicion to search and detain Abidor’s laptop because Abidor, a Ph.D. student in Islamic history, had pictures of Hamas and Hezbollah rallies on his computer, and because he possessed both U.S. and French passports. When the laptop was returned, evidence showed that agents had examined Abidor’s personal files, including photos and chats with his girlfriend.
When reporters cross borders, they are at increased risk of surveillance. As the 2013 federal district court case of Abidor v. Napolitano showed, border agents in much of the U.S. can search, copy, and detain a U.S. citizen’s laptop computer, cell phone, or other electronic device even when the agents have no reason to suspect any wrongdoing. The court held that the government had reasonable suspicion to search and detain Abidor’s laptop because Abidor, a Ph.D. student in Islamic history, had pictures of Hamas and Hezbollah rallies on his computer, and because he possessed both U.S. and French passports. When the laptop was returned, evidence showed that agents had examined Abidor’s personal files, including photos and chats with his girlfriend.
How, then, do reporters protect themselves and sources in an era of surveillance? At the TMC/IIT Chicago-Kent workshop, Gavin MacFadyen, Director of the Centre for Investigative Journalism at University College London, warned, “The first minute is the most crucial when the whistleblower calls a reporter.” At the workshop, a group of technical experts discussed technological tools and practices that journalists can use to protect themselves and their sources. Eva Galperin of the Electronic Frontier Foundation discussed threat modeling, in which a journalist or organization assesses potential threats to determine the level of protection needed. Threat modeling involves building a comprehensive list of people or entities who might be after information in one’s possession (say, an opposing lawyer, the NSA, or a foreign government). It then considers the nature of the information to determine the tools, such as encryption, which are required to protect it.
Once the level of threat is determined, reporters can use specific tools for defending against online surveillance. They can protect themselves and their sources by maintaining strong and unique passwords, detecting and avoiding fraudulent “phishing” emails, encrypting their laptops and other electronic devices, and using two-factor log-in authentication where available. They can protect anonymity with Tor, a powerful tool that works by obscuring the source and destination of online communications. They can use tools such as GPG to encrypt their emails and other communications and render them illegible to third parties.
Journalists can also use tools such as ObscuraCam, developed by the Guardian Project (unaffiliated with the U.K.’s Guardian news organization) to remove potentially identifying data from digital photos, and to obscure the faces of people appearing in photos in situations in which being identified might put them in danger. And news organizations can implement SecureDrop, a secure submissions system for receiving documents from anonymous sources.
No single tool or practice can render a journalist “NSA-proof” or immune to corporate spying, but appropriate tools and strong security practices can significantly evade surveillance and increase the reporters’ ability to deliver a well-researched, convincing story without exposing sources to harmful retaliation.


One of the most popular methods to access censored content is by using anonymous proxy servers, either in website form or software-based. The plan runs from a third celebration server and handles info exchange in between you and the servers you want to entry, these kinds of as internet sites, net mail, and chat rooms. They are message board “spammers” who are hired by big money special interest groups to deceive us into buying products or services that line the pockets of their employers.